Monthly Archives: November 2018
Apple Updates MacBook Air, Mac Mini and iPad Pro
Today’s topics include Apple updating the MacBook Air, Mac Mini and iPad Pro, and Bleedingbit Bluetooth vulnerabilities exposing WiFi access points to risk.Apple on...
OPNids Integrates Machine Learning Into Open-Source Suricata IDS
A new open-source intrusion detection system (IDS) effort is officially getting underway on Nov. 5 with the launch of the OPNids project.The OPNids effort...
Security Lessons Companies Can Learn From the U.S. Elections
The election race for the governorship of the state of Georgia promises to be tight, with current estimates showing that Democrat Stacey Abrams and...
T-Mobile Rolls Out Inexpensive Business Help Desk for Small Businesses
For the vast majority of small businesses, IT support means taking time away from an employee who is already doing something else to solve...
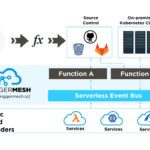
TriggerMesh Launches Kubernetes-Based Serverless Management Platform
A startup has emerged to take on the nascent space for serverless functions management. On Nov. 1 TriggerMesh officially launched, announcing a serverless management...
Cray Unveils Exascale Supercomputer for Running Complex Workloads
Today’s topics include Cray unveiling its first exascale supercomputer, Shasta, and LogRhythm advancing its NextGen SIEM security platform with security orchestration, automation and response...
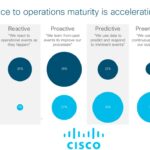
Cisco Measures the State of IT Operations Readiness
IT operations can be complex, and determining how mature and ready those operations are for change and innovation has long been a challenge for...
Customers Rank Trust Over Technology, LinkedIn Sales Report Finds
According to LinkedIn’s annual State of Sales report that surveyed more than 500 sales pros and 500 buyers in August 2018, establishing customer trust...
Bleedingbit Bluetooth Vulnerabilities Expose WiFi APs to Risk
Wireless access points from multiple vendors are potentially at risk thanks to a set of new Bluetooth flaws known as Bleedingbit.Bleedingbit was publicly announced...
Facebook Moves Swiftly to Limit Inauthentic Behavior on Social Network
Today’s topics include Facebook limiting inauthentic behavior, and Jamf releasing its Setup and Reset apps for iOS device management.As part of a renewed effort...