eWEEK content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More.
110 Tips for Identifying and Dealing With Phishing Email
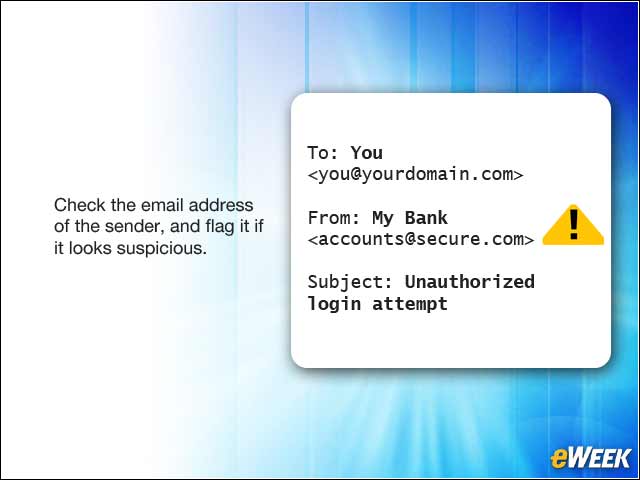
2Don’t Trust the Display Name
A favorite phishing tactic among cyber-criminals is to spoof the display name of an email. Here’s how it works: If a fraudster wanted to impersonate the hypothetical brand “My Bank,” the email may look something like the image here. Since My Bank doesn’t own the domain “secure.com,” email authentication defenses will not block this email on My Bank’s behalf. Once delivered, the email appears legitimate because most user inboxes and mobile phones will only present the display name. Always check the email address of the sender in the header; if it looks suspicious, flag the email.
3Don’t Always Trust the Sender’s Email Address
Fraudsters not only spoof brands in the display name, but they also spoof brands in the sender’s email address, including the domain name. Keep in mind that just because the sender’s email address looks legitimate (such as [email protected]), it may not be. A familiar name in your inbox isn’t always who you think it is.
4Look but Don’t Click
5Check for Spelling Mistakes
6Analyze the Salutation
7Watch What Information You Reveal
8Look at the Language in the Subject Line
9Review the Signature
10Be Cautious About Clicking on Attachments
11Don’t Believe Everything You See
Phishers are extremely good at what they do. Many malicious emails include convincing brand logos, language and a seemingly valid email address. Be skeptical when it comes to your email messages; if it looks even remotely suspicious, do not open it.