eWEEK content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More.
1Things Not to Do When Job Hunting
Wrote a Word macro virus that printed out his resume and demanded a job or he would write another malware to delete hard drives.Michael Buen, the author of the WM97/Michael-B Word macro virus, printed out his resume on Fridays towards the end of the month in infected documents. “Warning: If I don’t get a stable job by the end of the month I will release a third virus that will remove all folders in the Primary Hard Disk,” Buen warned. There was no applicable law to prosecute Buen at the time, according to the Philippines Supreme court.
2The Importance of Not Reusing Emails
Government authorities took years to track down a hacker who attacked Department of Defense computers. He was arrested after an email address used during the attack showed up in a resume posted on online job boards.Eduard Lucian Mandru’s 2006 hack of the U.S. Department of Defense computer system went unsolved for years. Authorities knew the attacker’s email address and came across it three years ago on a r??«sum??« that he’d posted on numerous job boards online.
3Hospital Audits Catch Snoopy Insiders
It seems that medical professionals cant resist looking up the case files of celebrity patients even if they dont have any need to access the information. Its easy to understand why star-struck hospital personnel cant resist looking up celebrity medical files. But these days even peeking can cost health workers their jobs. In recent years there have been egregious cases where celebrity patient data, perhaps most intimate of all personal information, have been lifted from hospital files and leaked to the tabloid media, presumably with money changing hands. Today, there are laws and regulations banning this kind of snooping. Modern computer systems generate audit trails so hospitals can comply with privacy laws. So hospital administrators along with law enforcement agencies and celebrity lawyers can find out who has been peeking at and even stealing patient information.
4Kelly Osbornes -Celebrity Hacker’
A hacker broke into Kelly Osbornes email account and forwarded new messages to personal account.An individual hacked into Kelly Osborne’s email account to read all her saved messages. The account was modified to forward new messages to another account, which turned out to be the hacker’s personal account. “This seemed like a pretty easy trail to follow,” said Alan Wlasuk, CEO of 403 Web Security.
5License Plates Can Be Traced
A hacker infected MySpace accounts, bragged about the exploit online and posted pictures of himself with his car’s license plate in the background.Samy Kamkar was responsible for the Samy Worm that infected more than 1 million MySpace accounts in 2006. He boasted what he did on a blog, which contained a picture of him with a license plate in the background, which was then used to find Samy.
6Dont Use Your Name
A hacktivist defaced a government site and signed his real name.A group of hacktivists that included one Shahee Mirza defaced a Bangladesh government military Website, mocking the government for weak security practices. “HACKERS R NOT CRIMINAL,” Mirza wrote, adding, “WE ARE GINIOUS.” He also left a banner HACKED BY SHAHEE_MIRZA.” “One can only imagine what the prisons are like in one of the poorest countries in the world,” said Alan Wlasuk, CEO of 403 Web Security.
7Benevolent Worms Can Still Have Teeth
A hacker released a worm that would download and patch vulnerable BIND DNS servers. The worm also contained a stealthy backdoor to give remote control and access of the infected system.Max Butler wrote and released a Linux ADM worm variant that attacked BIND DNS servers, downloaded and applied a patch to fix BIND vulnerabilities. The worm also maintained a stealthy backdoor that gave Butler or any other hacker in the know remote access and control of the systems. Butler claimed he never intended to use the backdoor.
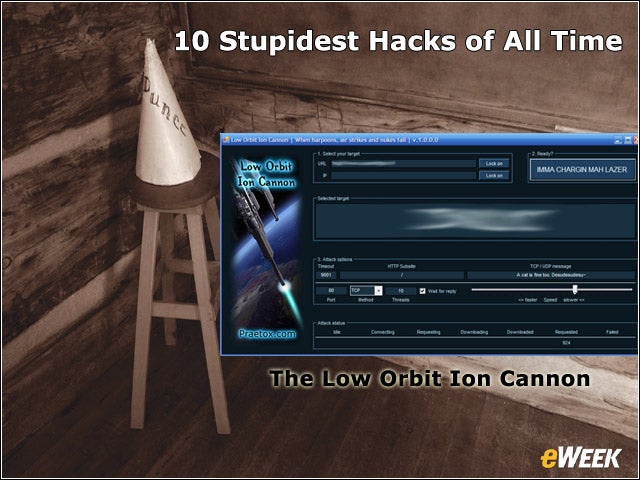
8Na???ve Hackers Will Get Caught
Newbies and enthusiastic activists didn’t realize the Low Orbit Ion Cannon tool used by Anonymous to launch distributed denial of services attacks didn’t mask user IP addresses, making them easier to find.The Low Orbit Ion Cannon allowed users to form a voluntary botnet to launch distributed denial of service attacks against companies severing times with WikiLeaks. The tool did not conceal the user IP address. “Hackers broke the No. 1 rule of attack: Wear a mask,” said Imperva’s Noa Bar Yosef.
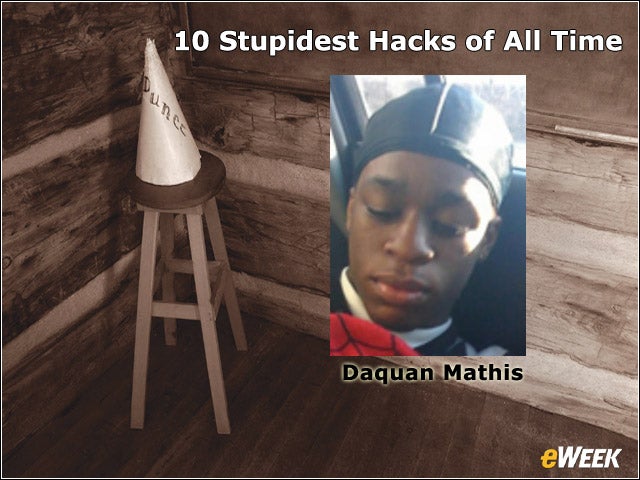
9Smile, You Are on Camera!
A man steals an iPhone, takes a photo of himself and sends it to his personal email account allowing the police to find and arrest the suspect.After Sayaka Fukuda had her iPhone stolen, she checked her iPhone email account online. The suspect, Daquan Mathis, had taken a picture of himself and sent it to his personal address, leaving the information behind in the sent-mail folder. Police used his email address and photo to track Mathis down and arrest him.
10Dumb or Clever?
Hacker uses a speed trap camera image to trick computers into wiping out database table.Some speed traps use cameras that automatically register the car’s speed and take a picture of the license plate. The camera’s character recognition technology translates the license plate image into a string that can be looked up in the department of motor vehicles database. The hacker changed his license plate number to ZU 0666, which was translated to a drop database table command. While the license plate number itself may have made it easy to track down the hacker, “this has got to be 10 out of 10 on the creativity scale,” said Alan Wlasuk, CEO of 403 Web Security.