By 2025, it’s estimated that 463 exabytes of data will be created daily; that’s the equivalent of 212,765,957 DVDs per day! Where is all this data going to be stored and who is responsible for keeping this information safe? This amount of data creates a large cyber-surface area and leads to its potential exposure.
Based on the most recent Pew Research survey, more than 81% of Americans believe they have little or no control over the data collected. At the same time, attackers are becoming more sophisticated: Criminal enterprises are pursuing the best market opportunities that minimize their costs and maximize profits. As enterprises, we must consider all possible ways data can be compromised to minimize exposure risks. Data privacy postures can be improved by focusing on protecting data of employees and customers as well as complying with privacy regulations.
Train your employees on best practices in data privacy
It is important that your internal house is in order at the same time you focus on the privacy of your customers’ data. Exposure of customer data by employees is one of the largest risks to data privacy, so everyone in the company must be trained on actionable steps they can take to protect their privacy and exposure of your customers’ data.
Best practices include:
- Employees must avoid downloading personal data from the network to their laptops. Data sitting on employee laptops is at higher risk of loss or theft than when it is maintained by internal systems with proper controls.
- Keep work and personal accounts separate; no company data containing personal information should be transferred to personal machines or accounts. Do not transfer any company data to cloud services that have not been approved. Tools may contain security vulnerabilities or carry greater disclosure risks than tools that have been vetted by your enterprise security team.
- Be wary of calls (or e-mails) from unknown individuals seeking information. There are cases of callers impersonating company personnel and claiming to need information desperately for a customer call or other urgent need. It is very easy to add the wrong email address to a message and send the wrong person sensitive or personal information.
Protect customer Personal Identifying Information (PII)
Are you prepared for a customer (PII) breach? While it’s a broad question, it’s probably one of the most important when it comes to protecting data and safeguarding your customers. Create a well-documented security incident and event strategy process. These exercises help your team gauge and improve the ability to handle security incidents and data breaches in the future. If you take a “privacy-by-design” approach to security, you approach your security projects by incorporating privacy and data protection from the start.
Best practices include:
- Managing customer data privacy is about creating a comprehensive governance framework that’s suited to your business. If you don’t know what data assets you hold, it’s difficult to assess what impact you might have from a data breach. You must identify and confirm with key stakeholders what data the organization stores or processes. This can be done via interviews that determine where your data repository locations reside.
- Your organization needs to keep a record of how and when data records are processed. Find out what systems use personal data records for processing and storage. This will help your security team understand how systems need to be protected, and they can help create a strategy for layered threat defense and protection.
- Encryption of data is key, yet most encryption software only encrypts information at rest or in transit, leaving sensitive data in plaintext and potentially vulnerable to exposure during processing. It is critical to review encryption and privacy data practices of your vendors and their vendors.
Comply with government privacy regulations
Demonstrating compliance with global data privacy regulations is a long-term outcome of implementing the right privacy and security controls with your people, processes, governance and technology. It requires a steadfast approach to each of these areas. There is enormous pressure on businesses and government to get behind a unified strategy and tame the data behemoth.
- Under the 2018 General Data Protection Regulation (GDPR) legislation, individuals can now request access to their data, find out if their data is being processed and request a transfer of their data to another system. You must put in place a mechanism by which to retrieve all their data and securely transfer the data to the individual.
- With new global data privacy laws, organizations need to take an in-depth look at how they acquire personal data of all types. This even includes basic personal data such as first and last name. Any personally identifiable information could be used by threat actors to compromise your network. And, under global data privacy laws, you can be fined heavily for a data breach with significant impact to individual data subjects.
- Your organization must be upfront, informative, concise and support lawful data processing. A privacy notice or policy must be delivered to data subjects before or as soon as reasonably possible after the organization collects their data. The privacy policy should be executed with key stakeholders in your organization, including legal, marketing and any other department that participates in active data collection and processing. Write your privacy policy in clear and plain language. Avoid legalese!
- You need to understand how data should be properly deleted or destroyed. Your employees need to know how and when to destroy or delete data. Your security department should also follow an industry standard like NIST’s Guidelines for Media for sanitizing and clearing storage devices.
- The California Consumer Privacy Act (CCPA), which went into effect Jan. 1, 2020, is soon to be replaced by California Privacy Rights Act (CPRA). The CPRA requires a business to provide greater disclosures in their notices of collection than what currently exists in the CCPA. The full 53-page text of the CPRA can be found here, most provisions of the CPRA, if adopted, will become operative in January 2023.
All these actions will lead you to have a better privacy and security structure in place. The sooner they are implemented, the greater success you will have in minimizing time and reducing the cost of a data breach.
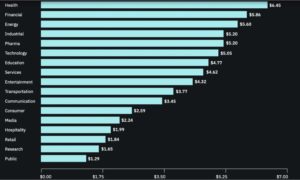
See this chart for time and cost estimates of data breaches across all industries:
[To see a larger view of this chart, click on it and select “Open in a New Tab.”]
Data breach costs correlate to the amount of time it takes to identify and contain the breach (the data-breach lifecycle). In 2020, a breach with a lifecycle of fewer than 200 days on average cost an organization only $3.21 million. But for a lifecycle greater than 200 days, the average cost jumps 30% to $4.33 million. Potential human error or system glitch can extend the lifecycle of the data breach and costs by millions of dollars.
The statistic, from IBM and the Ponemon Institute’s annual “Cost of a Data Breach” report, put a real-world price tag on the costs associated with a breach.
Businesses can improve their data privacy liability by having a data breach business continuity plan, automated encryption and security plans as well as complying with privacy regulations. Data breaches can impact a business for years; do not delay. Get started with your program today.