eWEEK content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More.
15 Deadly Sins of Privileged Access Management Put Firms in Harm’s Way
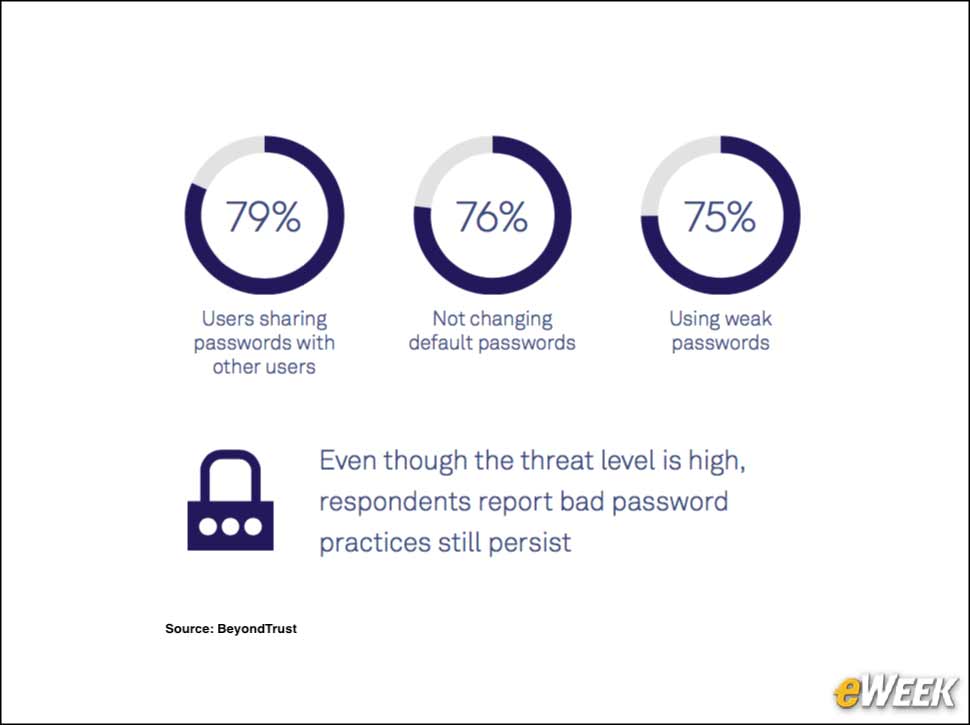
Data breaches continue to be a regular occurrence around the world as attackers exploit common weaknesses in enterprise infrastructure. A new report from security vendor BeyondTrust has identified what the company refers to as the “5 Deadly Sins” of privileged access management, which are actions and inactions taken by organizations that often lead to exploitable weaknesses. The 15-page report is based on a survey of 474 IT professionals from around the world. Among the survey’s findings is that 22 percent of organizations experienced security problems due to users sharing passwords with other users. The five deadly sins are password policy apathy, administrative privilege greed, patching pride, ignorance about privilege policies and cloud envy. In this slide show, eWEEK looks at the five deadly sins of privileged access management.
2Insecure Practices Lead to Security Problems
3Deadly Sin #1: Apathy
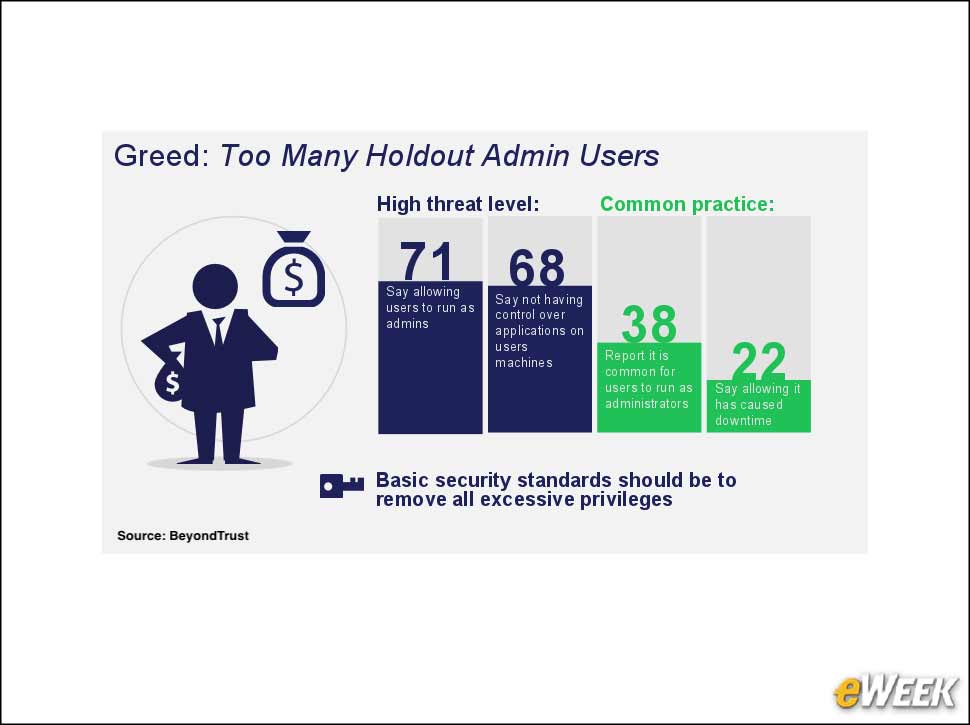
4Deadly Sin #2: Greed
5Deadly Sin #3: Pride
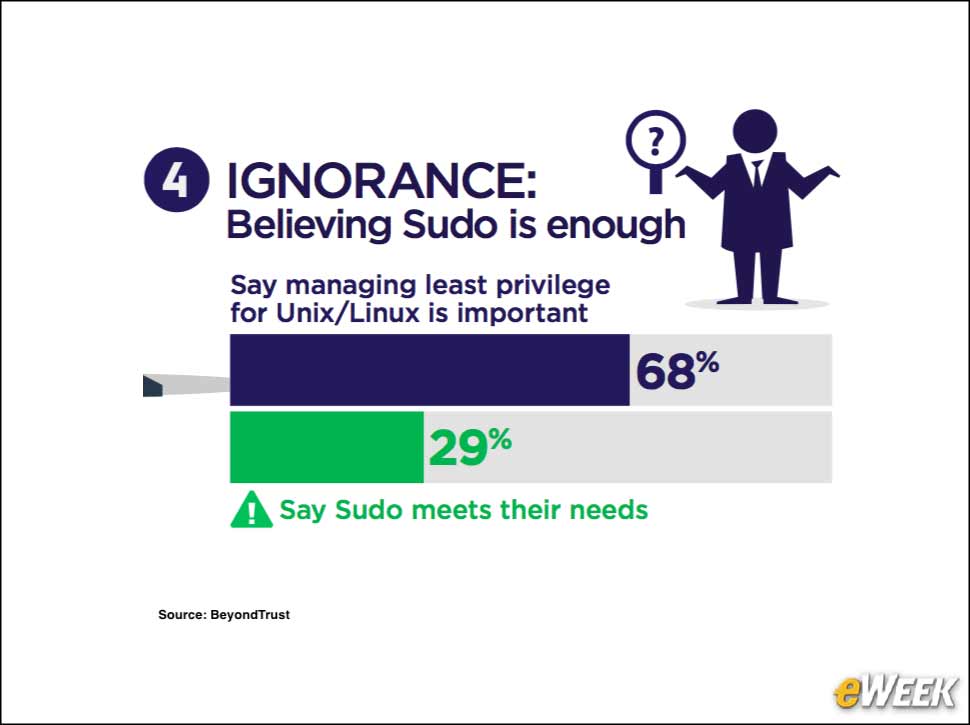
6Deadly Sin #4: Ignorance
Users frequently understand managing administrative access on a Linux/Unix system as simply using the Sudo command. With Sudo, a regular user potentially can temporarily elevate access to accomplish a specific task. The BeyondTrust study found that 68 percent of respondents said that managing least privilege on Linux/Unix is important, while 29 percent said Sudo is enough.
7Deadly Sin #5: Envy
Managing security and privilege access doesn’t stop when an application is delivered via the cloud in a software-as-a-service (SaaS) approach. BeyondTrust’s survey found that 37 percent of respondents said that they are not involved in protecting SaaS applications.