eWEEK content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More.
1Black Hat, DefCon Expose Flaws in Voting Machines to Smart Guns
The annual week of security conferences—the back-to-back Black Hat USA and DefCon events—colloquially referred to as “hacker summer camp” ran from July 22-30. The Black Hat show that was held at Mandalay Bay celebrated its 20th anniversary and was headlined by a keynote address from Facebook Chief Security Officer Alex Stamos. Perhaps the biggest single flaw detailed at Black Hat was the Broadpwn vulnerability that impacted hundreds of millions of iOS and Android devices. At the DefCon 25 conference, which was held at Caesar’s Palace, voting machines were hacked, as were internet of things (iOT) devices, cars, industrial control systems and even smart guns. In this slide show, eWEEK takes a look at some of the highlights of the 2017 Black Hat USA and DefCon conferences.
2Black Hat Now 20 Years Old
Jeff Moss, founder of both the Black Hat and DefCon security conferences, used the Black Hat keynote stage to reflect on the 20th anniversary of Black Hat. The Black Hat conference debuted five years after DefCon as a conference for security professionals, while DefCon is more of a hacker convention.
3Facebook Chief Security Officer Explains What’s Important
4Christian Slater Poses With Black Hat Attendees
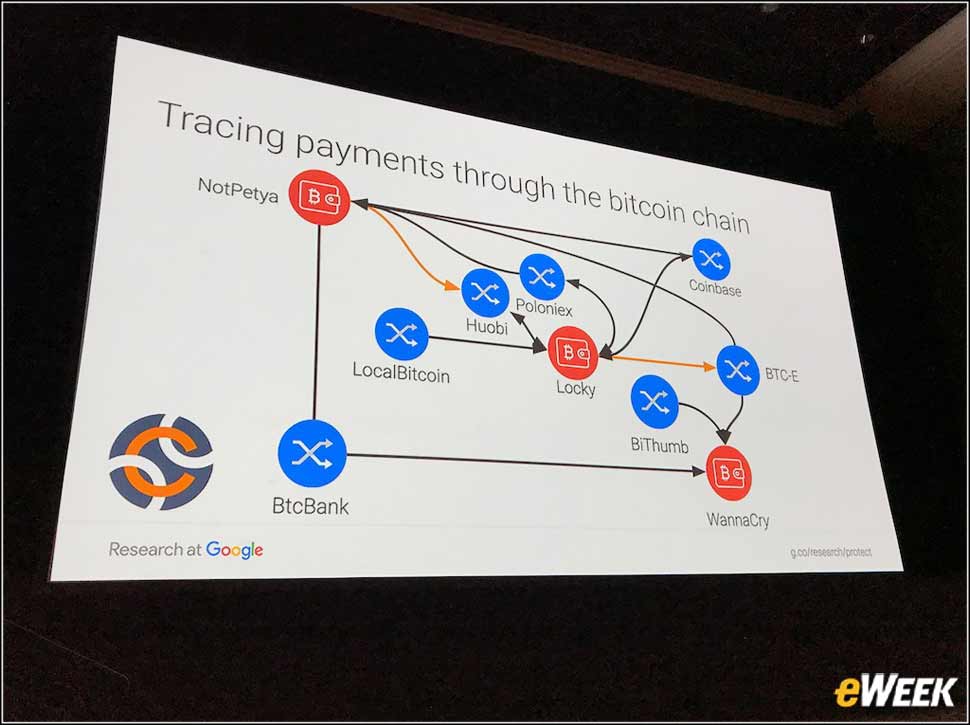
5Understanding Ransomware
6Broadpwn Flaw Revealed
Exodus Intelligence security researcher Nitay Artenstein detailed the Broadpwn vulnerability in Broadcom WiFi chips that impacted all iOS and Android devices. Thanks to Artenstein’s responsible disclosure to the impacted vendors, the flaws were patched several weeks prior to the Black Hat presentation.
7Voting Machines Hacked at DefCon
8Hacking All the IoT Things
9FTC Commissioner Explains How the Government Helps Security
10Hacking Cars at DefCon
11Taking Aim at Industrial Control Systems
12Make Your Own Tin Foil Hat
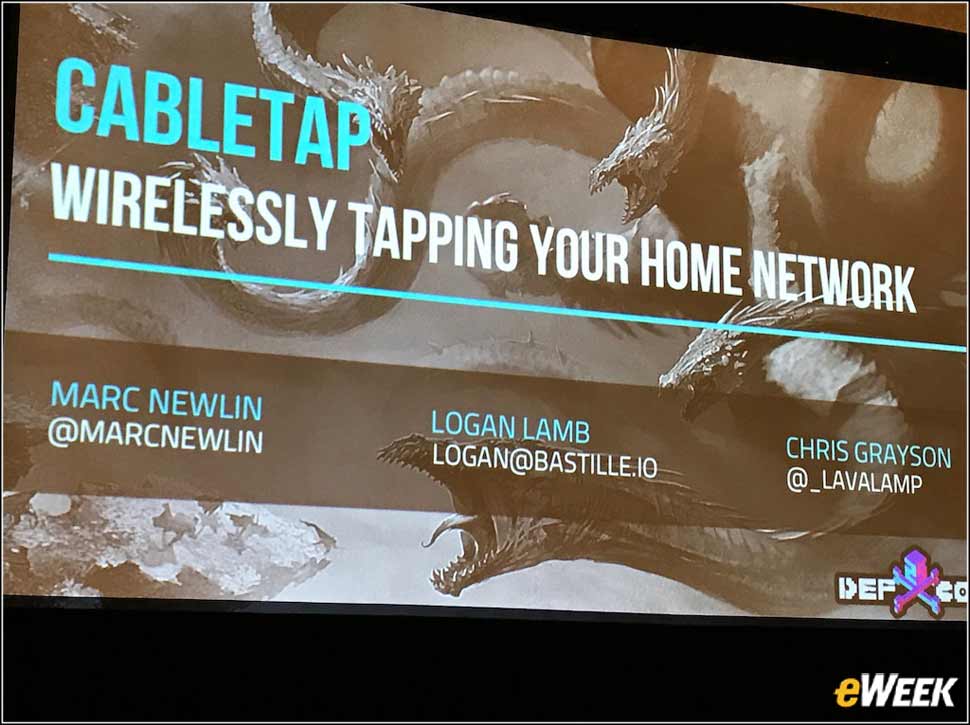
13Cabletap Vulnerabilities Revealed
14Smart Gun Apparently Not So Smart
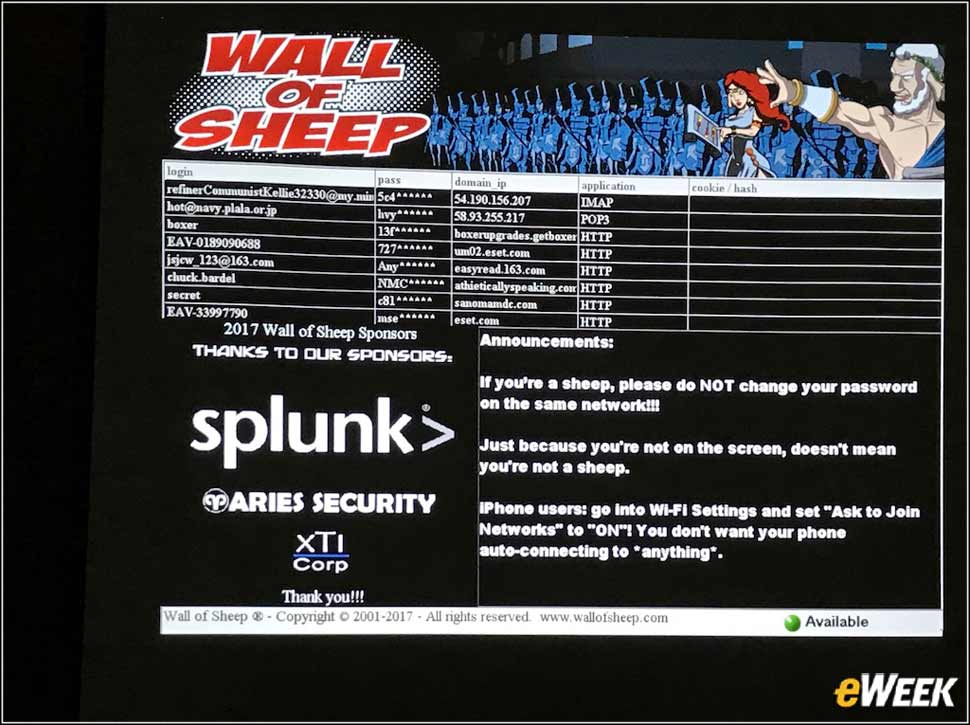
15Wall of Sheep Shows Insecure Users
16Black Hat Returns in August 2018
The Black Hat 2018 event is scheduled for Aug. 4-9, 2018.