eWEEK content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More.
2The MBR/Sinowal/Mebroot/Torpig rootkit—Stealthiest Rootkit in the Wild?
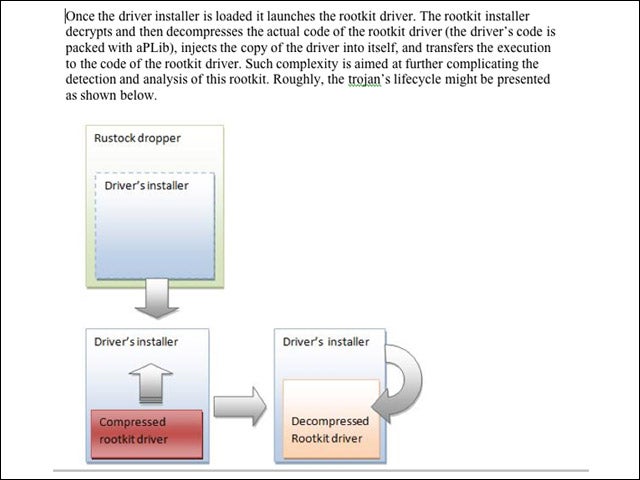
3Zeus—Malware from Mount Olympus
4Rustock.C—Busy Botnet
Rustock.C creates a back door on a compromised system and uses rootkit functionality to hide any files and registry subkeys it creates. The first “operational” samples of Rustock.C appeared in September 2007. Security researchers estimate the botnet can send out as many as 600,000 spam messages a day. Photo courtesy of Microsoft
5Vundo—Social Engineering
Vundo is a Trojan also known as Virtumonde. The malware has been linked to campaigns for rogue anti-virus. There are many different types of Vundo trojans. According to SecureWorks, the malware family includes rootkit functionality, and often spreads through Instant Messaging and fake YouTube videos. Once infected, victims may be hit with numerous payloads.
6No Title
Conficker—The Windows Worm You May Have Heard of Though it may have been overhyped, the Conficker worm definitely created a massive army of compromised computers. At various times, the number of infections has been put in the millions. More recent estimates have put the number of PCs compromised by variants A, B and C at about 2.7 million, according to the Conficker Working Group. Photo courtesy of Conficker Working Group
7Hexzone—Kidnapping Computers
Hexzone is installed as a “Browser Helper Object,” and injects itself into the browser as a plug-in. When the victim browses the Web, the plug-in leads them to a page hosting porn and demands payment to remove the content. According to FireEye, Hexzone has also been observed downloading Trojan.Ransomlock.
8Coreflood—A Deadly Banking Trojan
9Trojan Bankpatch.C—Denmark Banks Targeted
Bankpatch.C popped up earlier this year. Bankpatch is customized to target certain regions and certain banks, such as in January and February, when there was an outbreak of infections in Denmark. The first version of the Trojan was released in 2007, with the .C variant first appearing in August of 2008, according to Symantec.