eWEEK content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More.
2Trojans for Sale
3Infect Yourself? No Problem
4Master and Commander of the Cyber-Underground
5Room for One More
The subject of this slide is Trojan.Pilleuz, a worm that spreads through file-sharing programs, removable drives and Microsoft instant messaging clients. When executed, it connects to one or more of several network addresses and opens a backdoor on the compromised computer. The screenshot below shows the master console of the botnet after a newly infected system has joined. The worm is believed to stem from the Butterfly bot kit, which is no longer for sale.
6Clampi Infection Rates
7Stealing the Data
8Stealing the Data, Reloaded
9Malicious Links Leading to Malware
We end at the place where it all starts for phishing victims—the infection. In the example here, the user is tricked into visiting a malicious site. This one promises the visitor information about the “murder” of pop star Michael Jackson. All users have to do to get infected is click on the link on the page.
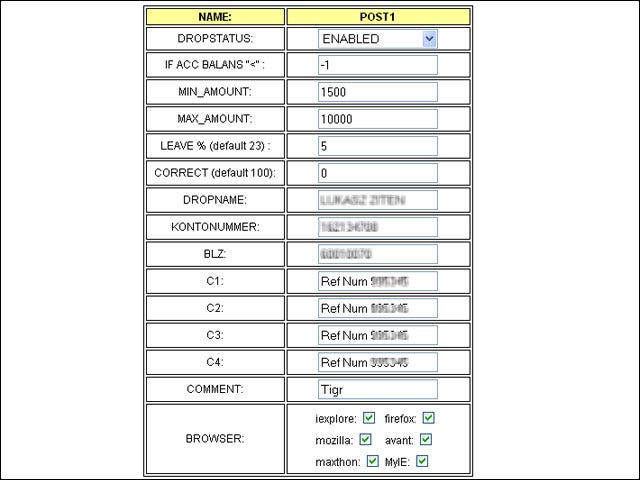
10Money Mules Transfer Profits
In the case of the URLZone Trojan, the gang behind it uses money mules to get the money from the stolen accounts. Here is a money mule definition screen that includes the maximum and minimum amount to steal, the money mule account details, enable/disable flags and the comments for the fraud transaction (money transfers often include comments such as the reason for transferring the money, Finjan researchers explained).