eWEEK content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More.
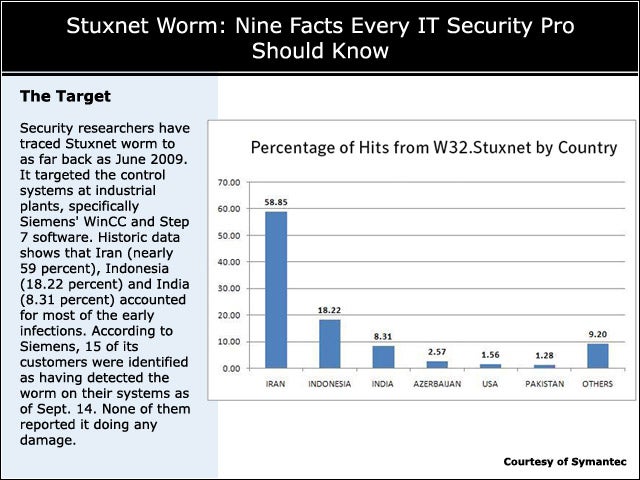
2The Target
Security researchers have traced Stuxnet worm to as far back as June 2009. It targeted the control systems at industrial plants, specifically Siemens’ WinCC and Step 7 software. Historic data shows that Iran (nearly 59 percent), Indonesia (18.22 percent) and India (8.31 percent) accounted for most of the early infections. According to Siemens, 15 of its customers were identified as having detected the worm on their systems as of Sept. 14. None of them reported it doing any damage.
3Digital Certificates to Go
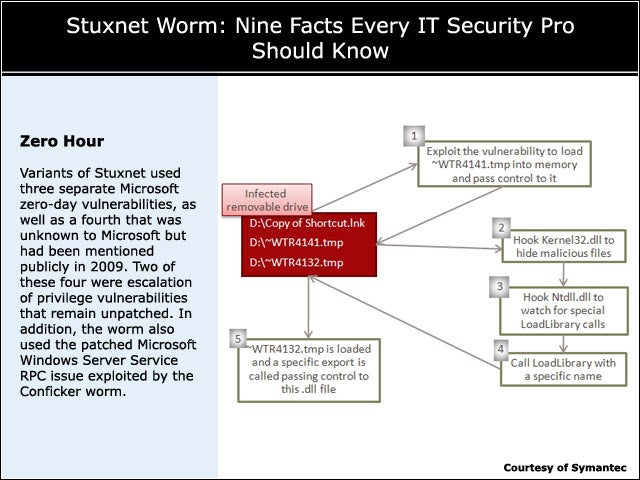
4Zero Hour
Variants of Stuxnet used three separate Microsoft zero-day vulnerabilities, as well as a fourth that was unknown to Microsoft but had been mentioned publicly in 2009. Two of these four were escalation of privilege vulnerabilities that remain unpatched. In addition, the worm also used the patched Microsoft Windows Server Service RPC issue exploited by the Conficker worm.
5Before the .LNK Vulnerability
The first zero-day publicly associated with Stuxnet was a vulnerability involving the loading of .LNK files on Windows. But before that, early versions of Stuxnet abused Windows’ AutoRun feature to spread. Rather than use an actual vulnerability, the malware took advantage of the way AutoRun processes commands from autorun.inf files to get the system to execute the worm’s malicious code.
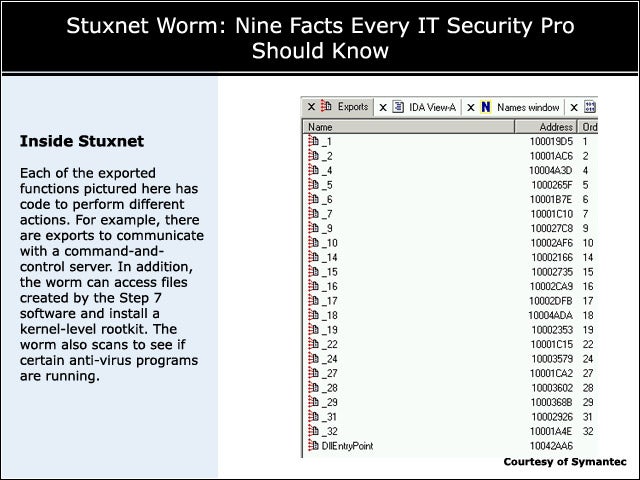
6Inside Stuxnet
Each of the exported functions pictured here has code to perform different actions. For example, there are exports to communicate with a command-and-control server. In addition, the worm can access files created by the Step 7 software and install a kernel-level rootkit. The worm also scans to see if certain anti-virus programs are running.
7Be Fruitful and Multiply
Researchers have uncovered multiple propagation vectors for the worm. In addition to using infected USB devices, the worm also copies itself to network shares protected by weak passwords. Stuxnet also has the ability to upgrade through peer-to-peer, giving the attackers the ability to be updated after the initial command-and-control server was disabled. Pictured here is a map of infections.
8The Discovery
9The Solution
As the weeks wore on, Microsoft patched some of the vulnerabilities associated with the worm, while security vendors issued detection for it. For its part, Siemens distributed a tool developed by Trend Micro to help companies clean their systems. This graph depicts recent infection levels worldwide.
10Cyber-war?
An open-ended question due to Stuxnet’s sophistication is whether the malware was created on behalf of an intelligence agency to disrupt industrial systems, particular in light of the fact that Iran’s first nuclear power plant was found to have been infected. Others have suggested it could have been done by a well-funded team of experts. While no firm evidence of state-sponsored activity has been uncovered, several security analysts have described it as a wakeup call for SCADA security.