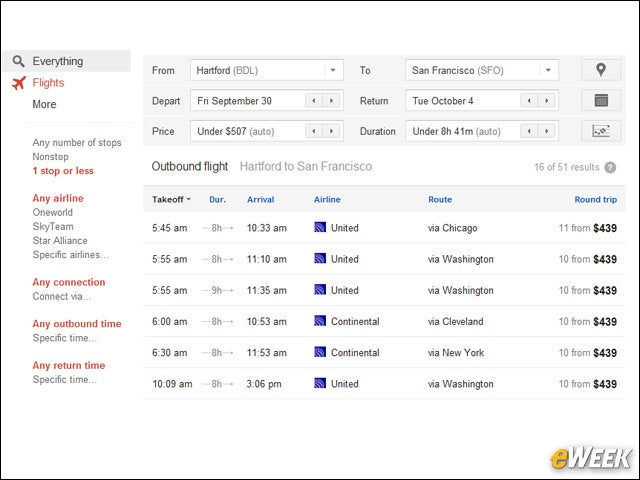
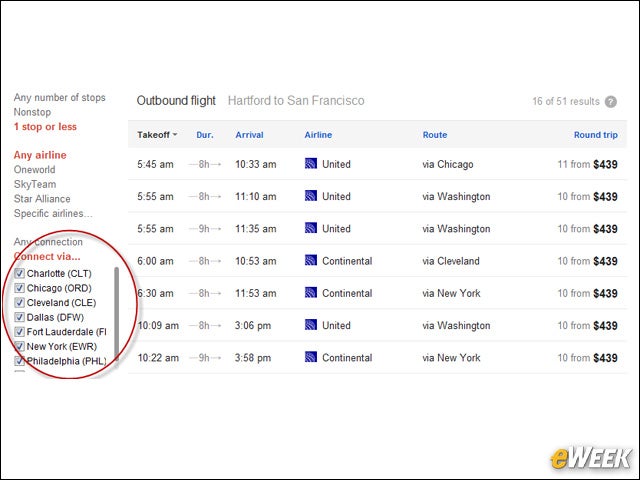
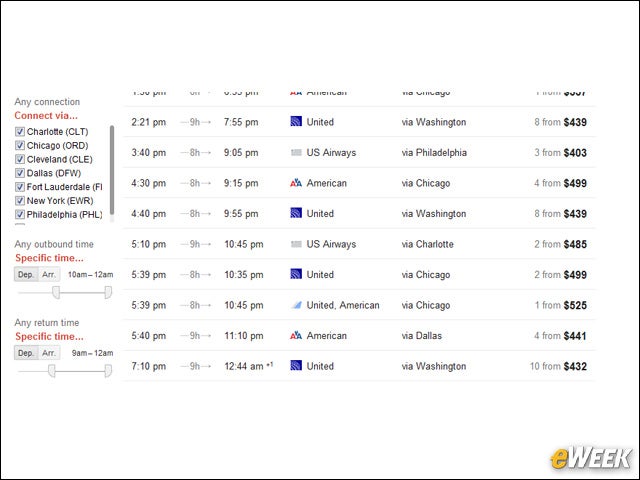
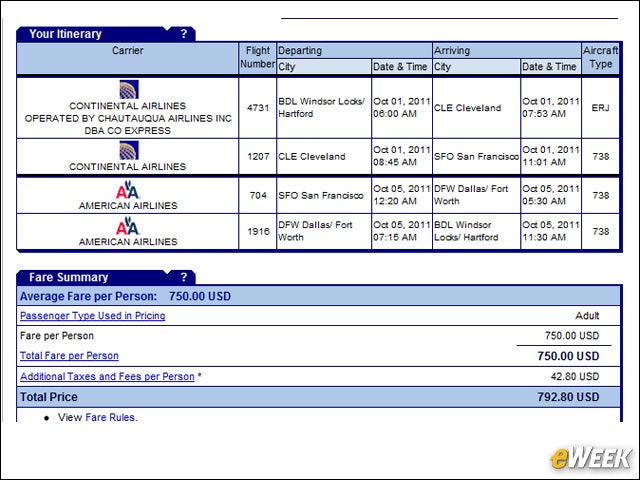
eWEEK content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More.
2The 15 Most Influential People in Security Today – 1. Tavis Ormandy, Google Security Team
As goes Google, so goes Web 2.0 security. Tavis Ormandy, one of the most visible hackers/researchers on the Google Security Team, faces the unenviable responsibility of making sure all of Google’s products pass the security smell test. An open-source security guru, Ormandy is tasked with identifying and analyzing vulnerabilities and exploits–and with getting them fixed before the bad guys can do damage. He is also co-lead of the Gentoo Security Team, shoring up the security of the Linux distribution.
3The 15 Most Influential People in Security Today – 2. Ivan Krstic, One Laptop Per Child
4The 15 Most Influential People in Security Today – 3. Chris Paget, IOActive
Chris Paget’s demonstration of an RFID cloner at last year’s Black Hat and RSA Security conferences helped to draw attention to major weaknesses in a technology that’s becoming more and more mainstream. He showed how easy it is to build a working RFID tag cloner as part of a larger effort to underscore the insecurity of wireless technology.
5The 15 Most Influential People in Security Today – 4. Bunnie Huang, Bunnie Studios
The frontier of computer security isn’t the next Windows operating system; it’s the tiny computers embedded into everything we make, from cell phones to microwaves to alarm clocks. And the most visible person working out in the Wild West of hardware hacking is Bunnie Huang. Huang is an MIT PhD, founder of Chumby, breaker of the original Xbox and referee of the monthly “Name That Ware” contest. What-
6The 15 Most Influential People in Security Today – 5. Michal Zalewski, Google
Before joining the search marketing giant as an information security engineer, Michal Zalewski launched an all-out assault on the security models of modern Web browsers, exposing critical vulnerabilities in Microsoft’s Internet Explorer and Firefox. His public disclosure of those flaws went a long way to hardening the browsers. Now a member of Google’s security team, he continues to find and report bugs in Apple’s Mac OS X and to use his hacking skills to help secure Google’s long list of Internet-facing products.
7The 15 Most Influential People in Security Today – 6. Window Snyder
A former Microsoft security strategist, Window Snyder borrowed a page from Redmond’s playbook and introduced a comprehensive-threat modeling and penetration-testing routine to Mozilla, where she now works as “Chief security something or other…” Snyder’s behind-the-scenes security efforts–which include outside hacker teams conducting simulated attacks on Firefox 3–are sure to pay off for the open-source alternative Web browser.
8The 15 Most Influential People in Security Today – 7. The MOAB Hackers
Spurred on by apathy–some would say arrogance–of the Mac faithful toward security, a group of hackers decided to document and disclose vulnerabilities in the Apple ecosystem every day throughout the month of January. What followed was the “Month of Apple Bugs,” an eye-opening effort that forced Apple’s security response team into action and helped speed up the delivery of security updates from Cupertino.
9The 15 Most Influential People in Security Today – 8. Dino Dai Zovi
Where the “Month of Apple Bugs” exposed Mac OS X security holes in a theoretical way, New York-based researcher Dino Dai Zovi took it a step further, launching a remote code execution attack against a fully patched MacBook Pro as part of a contest at the CanSecWest security conference. Dai Zovi’s attack confirmed for many that malware-delivery attacks against Apple’s OS are a reality.
10The 15 Most Influential People in Security Today – 9. Michael Howard, Microsoft
11The 15 Most Influential People in Security Today – 10. HD Moore, Metasploit
A rock star in hacker circles, HD Moore continues to push the vulnerability research envelope with his free Metasploit exploit development and penetration testing framework. The freely available point-and-click hacking tool is constantly refreshed to keep pace with security research, and now includes built-in support for breaking into Apple’s iPhone, full support for the Windows platform (including GUI) and more than 450 modules and about 265 remote exploits.
12The 15 Most Influential People in Security Today – 11. Dave Aitel, Immunity
Founder of the widely read Daily Dave mailing list and a skilled hacker in his own right, Dave Aitel’s delivery of proof-of-concepts and exploits in the commercial CANVAS attack tool go a long way toward helping businesses and IDS (intrusion detection system) vendors determine risk from known–and unknown–vulnerabilities.
13The 15 Most Influential People in Security Today – 12. Bronwen Matthews, Microsoft
A key part of Microsoft’s mandatory SDL process is Bronwen Matthews’ responsibility. A Trustworthy Computing security program manager, Matthews manages the vendor selection process for security researchers, penetration testers and expert instructors. In this role, she controls the budget for outside hacking teams hired to break Microsoft’s products, spreading her influence in two parts: security of the Windows ecosystem and, more importantly, funding the startups that promote the best in security research.
14The 15 Most Influential People in Security Today – 13. John Pescatore, Gartner
15The 15 Most Influential People in Security Today – 14. Rob Thomas and Team Cymru
16The 15 Most Influential People in Security Today – 15. Stefan Esser, Hardened PHP Project
If there’s a security hole in PHP, chances are it was found by Stefan Esser, an open-source security specialist. Esser’s advisories about flaws in Linux, NetBSD, Samba, Ethereal, CVS, Subversion, MySQL and PHP are legendary. He is also known as the first hacker to completely break the DRM (digital rights management) scheme of the Microsoft Xbox with software-only exploits. His “Month of PHP Bugs” project thoroughly exposed the insecure nature of the widely deployed PHP language and forced a rethink about security in the open-source world.