eWEEK content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More.
3No Title
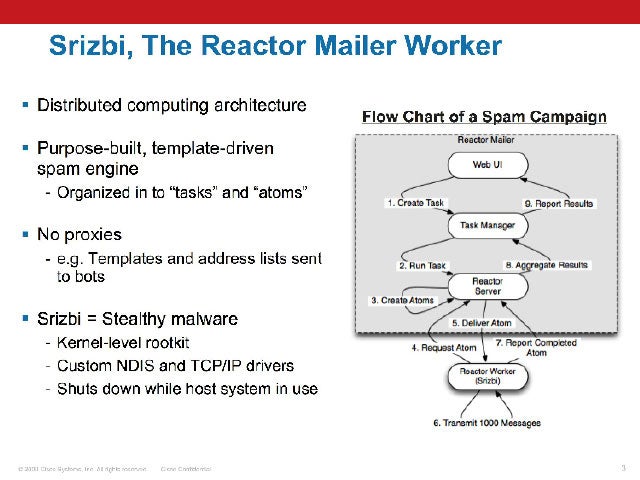
Birth of a Botnet
The first reports of the botnet surfaced in 2007. Srizbi spread through a Trojan deployed by various malware toolkits, most notably MPack. The botnet would spam out messages containing malicious links that would lead to the malware kit. MPack was also known to spread via compromised Websites.
4No Title
5No Title
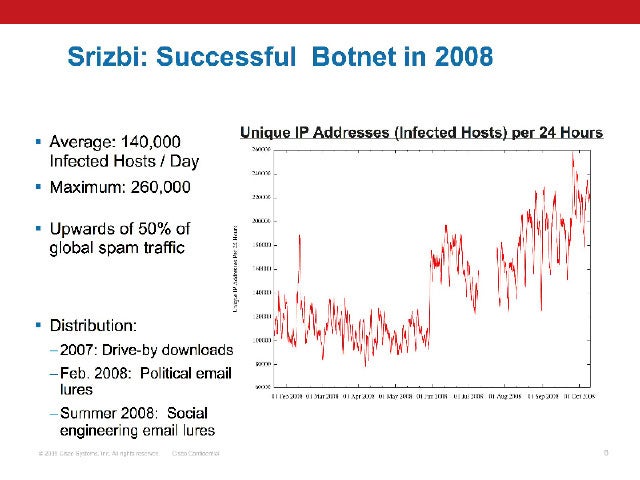
Botnet Blasting Spam
According to Cisco, at its height, Srizbi could send out more than 100 billion spam messages a day. One of the most well-known spam campaigns tied to Srizbi is the so-called “Ron Paul Incident,” where the botnet blasted out e-mails promoting a run for president by the Texas congressman.
6No Title
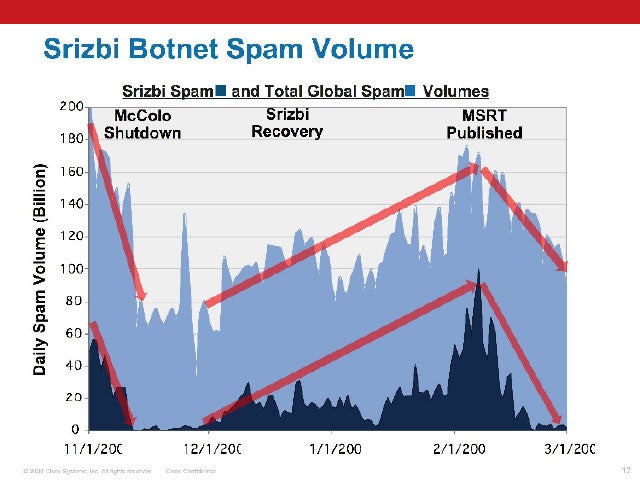
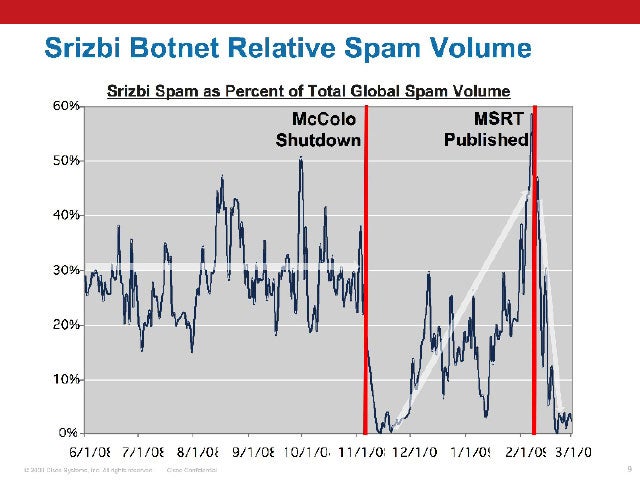
The Fall of Srizbi
After a combination of investigative reporting by the Washington Post and the efforts of the security community, notorious Web hosting firm McColo is shut down. Spam plummets. Srizbi, as the diagram shows, starts to make a small comeback, but is stopped dead in its tracks courtesy of an update to Microsoft’s Malicious Software Removal Tool (MSRT).
7No Title
There’s Dead, and Then There’s Dead
Even though the botnet is on its deathbed, the minds behind it are reportedly still hard at work trying to infect new victims. According to Cisco, the minds behind it are now in control of the Xarvester botnet, which controls about 100,000 hosts. Though considered two separate botnets, they share common nodes, and the Reactor Mailer front end is common to both.