eWEEK content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More.
1Whodunit? Finding Security Vulnerabilities in Application Code
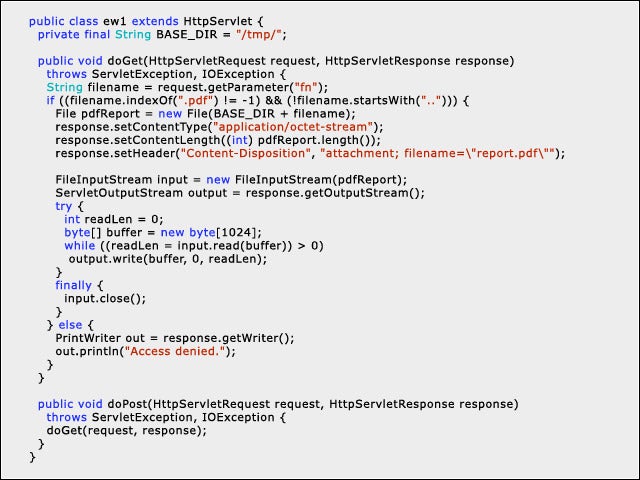
2File/Path Manipulation
3The Answer
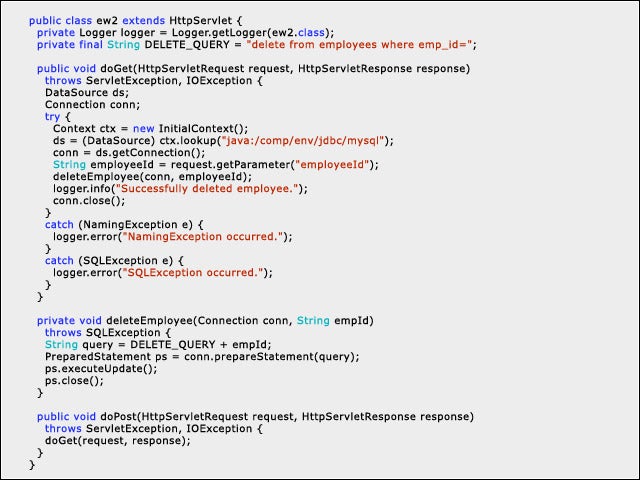
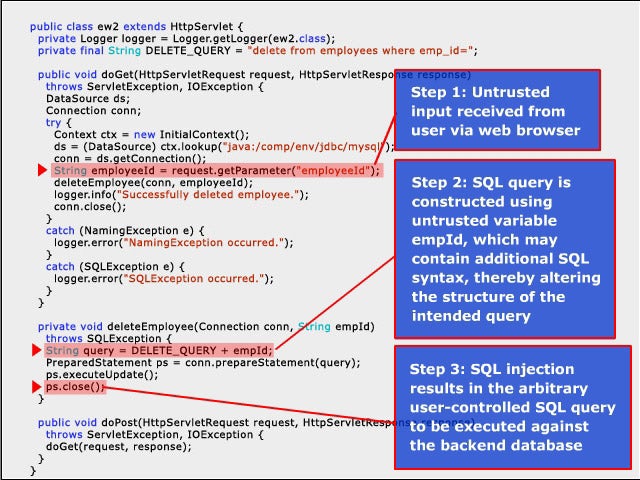
4Hands Off the Database
SQL injection is one of the most popular vectors of attack. When executed, the SQL statement fetches a different set of results from the database than the application would have originally requested. The attacker gains unauthorized access to or manipulates the data residing in the database on the server.
5The Answer
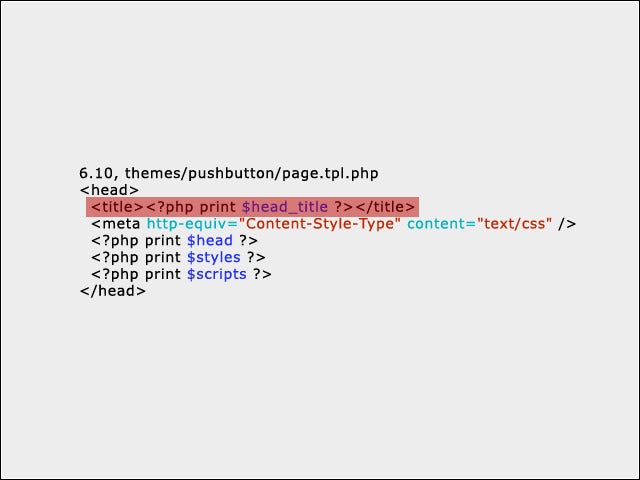
6Solving Cross-site Scripting
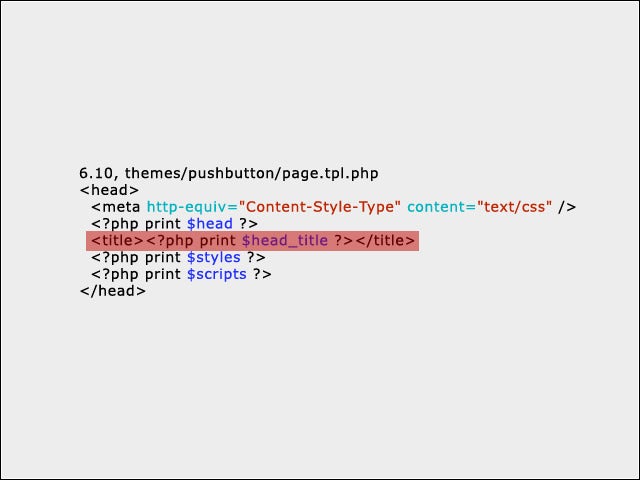
7The Answer
In this case, moving the <title> to after the <meta> tag prevents XSS attacks that trick the browser into using UTF-7 to decode the payload when the page should be actually rendered as UTF-8.