eWEEK content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More.
1Why DNS Servers Are an Unprotected Back Door into Your Network
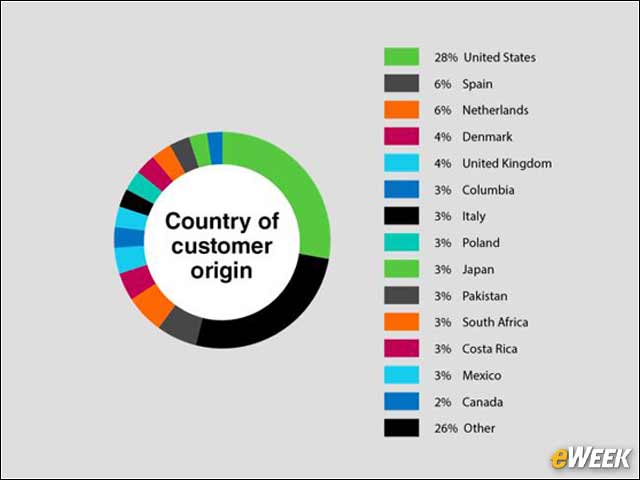
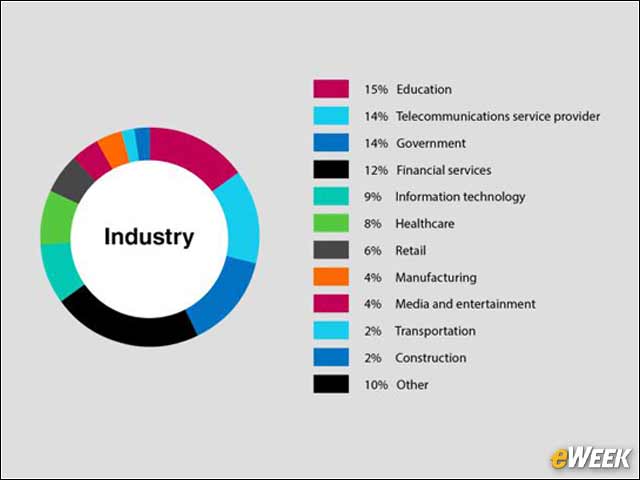
2Analyzing DNS Data
3U.S. Far and Away the Biggest Target
4Education Leads Most Vulnerable Sectors
5Protocol Anomalies: 48 Percent
6DNS Tunneling: 40 Percent
DNS tunneling enables cyber-criminals to insert malware or pass stolen information through DNS, thereby using DNS as a covert communication channel to bypass firewalls. While there are semi-legitimate uses of DNS tunneling, many instances of tunneling are malicious. Several off-the-shelf tunneling toolkits are readily available on the internet, so hackers don’t always need technical sophistication to mount DNS tunneling attacks.
7Botnets: 35 Percent
8Amplification and Reflection Traffic: 17 Percent
Reflection attacks use one or more third-party DNS servers, usually open resolvers on the internet, to propagate a distributed denial of service (DDoS) attack on a victim’s server. Attackers spoof the DNS queries they send to open resolvers by including the victim’s IP address as the source IP. The resolvers send all responses to the victim’s server, thereby overwhelming it and potentially creating a denial of service. In an amplification attack, the queries are specially crafted to result in a very large response. Cyber-criminals typically use a combination of amplification and reflection to maximize impact on the victim’s server.
9Distributed Denial of Service (DDoS) Traffic: 14 Percent
DDoS attacks use hundreds or even thousands of hosts to flood a target with traffic, such as DNS requests, with a goal of knocking the targeted site offline. Some DNS-based DDoS attacks use “phantom domains” to either keep a DNS resolver engaged by making it wait for responses or by sending random packets. The DNS resolver consumes valuable resources while waiting for valid responses, resulting in poor or no response to legitimate queries.
10Ransomware: 13 Percent
Ransomware, such as CryptoLocker, encrypts files on a computer’s local hard drive or mapped network drives by getting an encryption key from an internet-based server. Users are then asked to pay a ransom to restore access to their data. One way of stopping ransomware is by blocking an infected system from accessing the malicious encryption servers by preventing DNS queries to them.
11What Can You Do Now?
When suspicious DNS activity is detected, whether from the internet or from within a company’s network, network administrators and security teams can use DNS security tools to quickly identify attacks and drop them; use DNS firewalling to prevent malware inside the network from communicating with command-and-control servers or exfiltrating data; and automatically remediate infected devices using ecosystem integrations with other security tools.