Monthly Archives: July 2013
IBM Touts BLU Acceleration Big Data Technology Now in DB2
IBM recently announced strong client and business partner support for the new version of its DB2 database software.Now generally available, the new software—which represents...
Dell Buyout: Icahn Gets Funding, Demands Meeting With Directors
With the vote on Dell's future less than three weeks away, investor Carl Icahn is again pressing the company's board of directors to consider...
Google Reader Deserved to Die: 10 Reasons Why
Google Reader Deserved to Die: 10 Reasons Why
by Don Reisinger
The RSS Feed Is Losing Steam
When Google Reader launched in 2005, it was based on...
Companies Lack Real-Time Breach-Detection Capabilities: Survey
More than 40 percent of security professionals have no or very limited automated capabilities, including real-time alerts or daily/weekly reporting, to detect data breaches,...
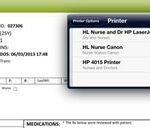
Chen Medical Prints Health Records From iPad, Android Tablets
Despite the ongoing move to electronic health records (EHRs) in health care, many doctors still prefer to print out documents and make annotations on...
Gartner Cuts 2013 IT Spending Forecast Due to PC Market Weakness
Gartner analysts are reducing their forecast for worldwide IT spending for 2013, due in large part to the continued decline of PC sales.Gartner is...
Google Adds BYOD Management Tools for Android
Google has just unveiled new Android bring-your-own-device (BYOD) management tools for enterprise IT teams to help them improve and tighten their management of user...
HP Plans to Get Back Into Smartphones, Official Says
A Hewlett-Packard official is reiterating the company's intention of re-entering the highly competitive smartphone market.Speaking to the Indian Express news site, Yam Su Yin,...
Mozilla Firefox OS Smartphones Make Their Way Into the World
Mozilla has been promising smartphones running on its Web-based Firefox OS, and on July 1 it showed off the Alcatel One Touch Fire and...
Cyber-Attackers Constantly Hitting Gas Utilities in 2013
Unknown attackers have targeted the Internet-connected systems of natural-gas companies, using brute-force attacks to attempt to access the companies' business and process-control networks, according...