Monthly Archives: August 2014
Boosting Your Online Privacy: 10 Best Practices
Boosting Your Online Privacy: 10 Best Practices
By Don Reisinger
Maximize Your Browser's Privacy Settings
Your browser's privacy settings might not be the panacea that will protect...
Spam Spikes and Java Exploits Continue to Grow
Cisco released today its 2014 Midyear Security Report, and it contains some trends that are the same as those the company detailed in its...
Why Mobile Apps Fail and How to Improve Them
Why Mobile Apps Fail
by Darryl K. Taft
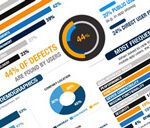
Behind the Data
Perfecto Mobile gained insight from an audience that knows mobile app development and testing the best—nearly...
Solix Launches Big Data Suite for Hadoop
Enterprise data management (EDM) specialist Solix announced the launch of Big Data Suite, an enterprise archiving and data lake application platform for Apache Hadoop.The...
Android Captures 85 Percent of Smartphone Market Worldwide
The Google Android operating system captured a new record of 85 percent global market share, mainly at the expense of BlackBerry, Apple iOS and...
Runtastic Orbit Fitness Tracker Monitors Exercise, Sleep
Health and wellness technology specialist Runtastic unveiled its first hardware product, the Orbit, a 24-hour tracking device that allows users to track their daily...
Dell Server Executive Says ARM Server Market Uncertain
Dell over the past couple of years has been among the highest-profile server makers looking to help bring 64-bit ARM-based chips into the data...
FCC Ban on Joint Sprint, T-Mobile Spectrum Bid Casts Shadow Over Merger
In what may be the first of many blows to plans by T-Mobile and Sprint to merge, the Federal Communications Commission is saying that...
Mobile Phones at Risk From Carrier Backdoor Flaw: Black Hat
Hidden within hundreds of millions of mobile phones around the world is control software used by carriers to help set up devices and features....
Black Hat, DefCon Talk to Focus on Smartphone Security, USB Flaws
Digital security is much in the news this week as the annual Black Hat and DefCon events convene in Las Vegas. New hacks, new...