eWEEK content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More.
1Comodo AEP Applies AI to Constant Battle Against Ransomware, Malware
Comodo’s Advanced Endpoint Protection (AEP) brings multiple cloud and endpoint technologies together to battle malware threats. AEP combines a cloud-based IT and Security Manager (ITSM) console with an endpoint client (Comodo Client) and an artificial intelligence-powered file analytics platform called Valkyrie. ITSM is designed to unify the management of Comodo products and endpoints across an enterprise. As a subset, ITSM focuses on the security and management aspects of enterprise as well as on enforcing security rules and policies. The Comodo Client is a locally installed piece of software that combines several forms of malware and privacy protection into a small package that can leverage Valkyrie, which uses AI-based analytics to determine whether malware lurks inside files.
2Get Started With Comodo One Enterprise Portal
The Comodo One Enterprise Portal is the primary management console for all of Comodo’s enterprise products. Administrators can use the portal to launch numerous other tightly integrated management consoles and control multiple aspects of endpoint security. Administrators can also implement a service desk, control domain security and run ITSM from the portal.
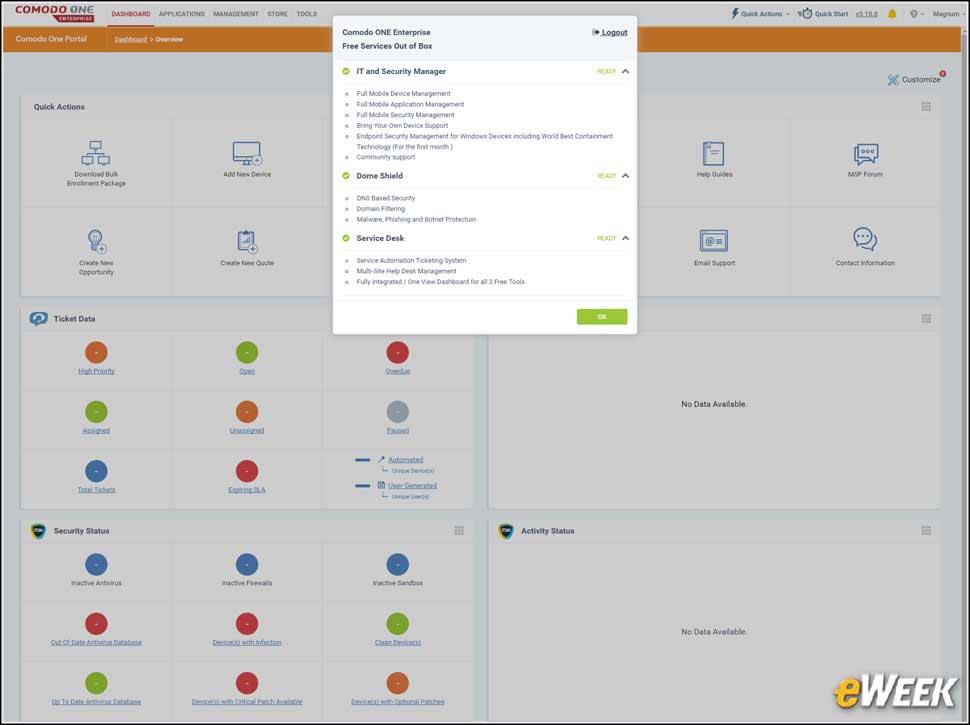
3Comodo One Enterprise Portal Is Customizable
The Comodo One Portal is customizable, allowing administrators to hide or expose widgets that make up what is displayed on the dashboard. With AEP, most of the management takes place in ITSM, so administrators not using Comodo’s other products may want to shut off any widgets not related to endpoint security.
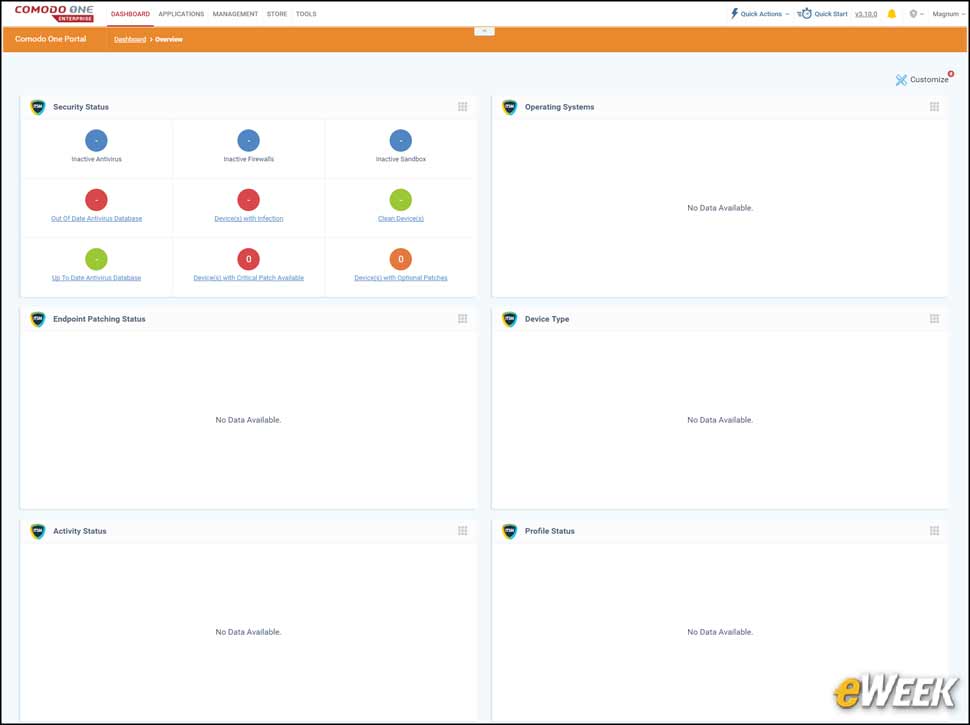
4Critical ITSM Functions Managed on Dashboard
5Manage System Security Through the ITSM Dashboard
ITSM has a well-defined dashboard in its own right, and administrators leveraging AEP will probably spend most of their time managing systems and security here. The dashboard also supports the deployment of clients, the registration of users and endpoints, and a reporting module that displays numerous pieces of information related to the security on an endpoint.
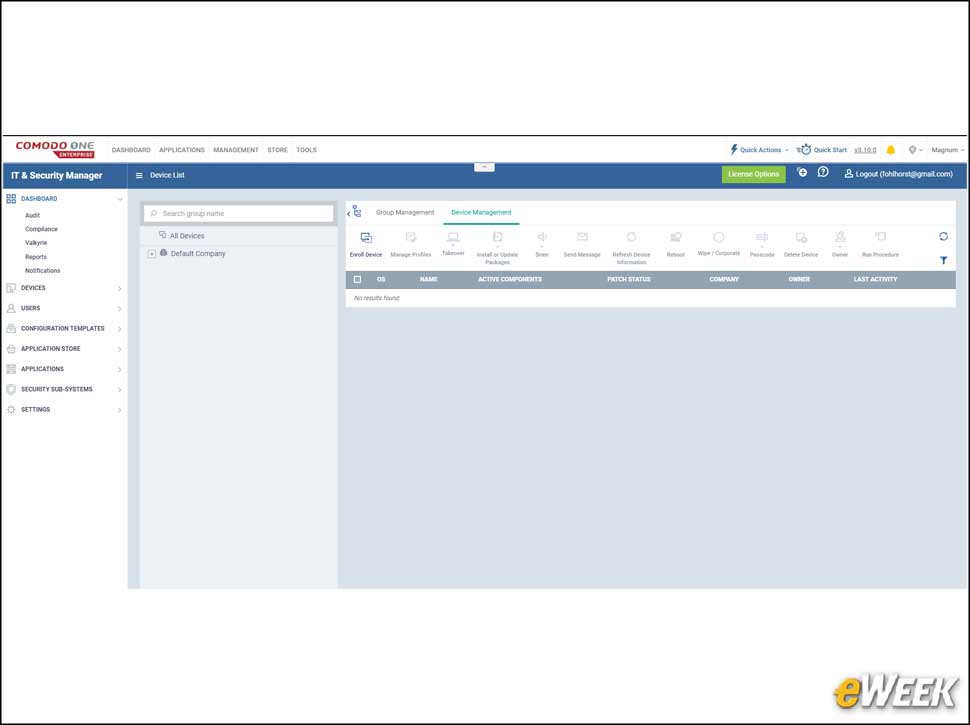
6Registering Endpoints Proves Easy With ITSM
For ITSM to manage endpoints, they must be registered with the system. Device registration is very easy, and there are numerous ways to register a device. Smaller organizations, for example, may seek to have the actual users of the endpoint register their device, a process that is initiated by sending an email to the user, who then clicks on a link to register the device as well as install the Comodo Client.
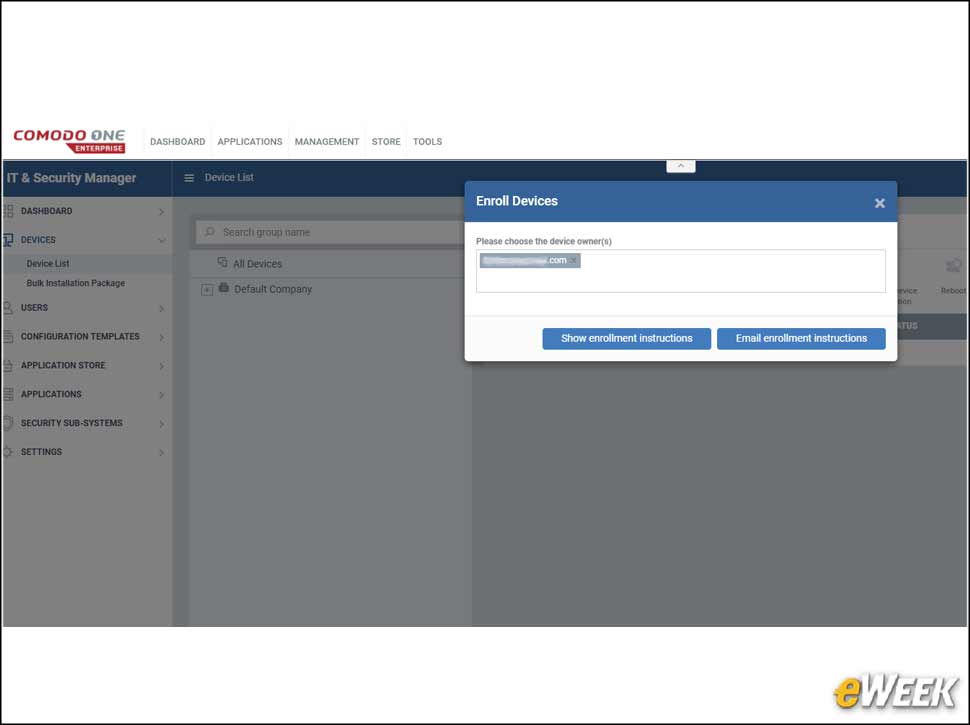
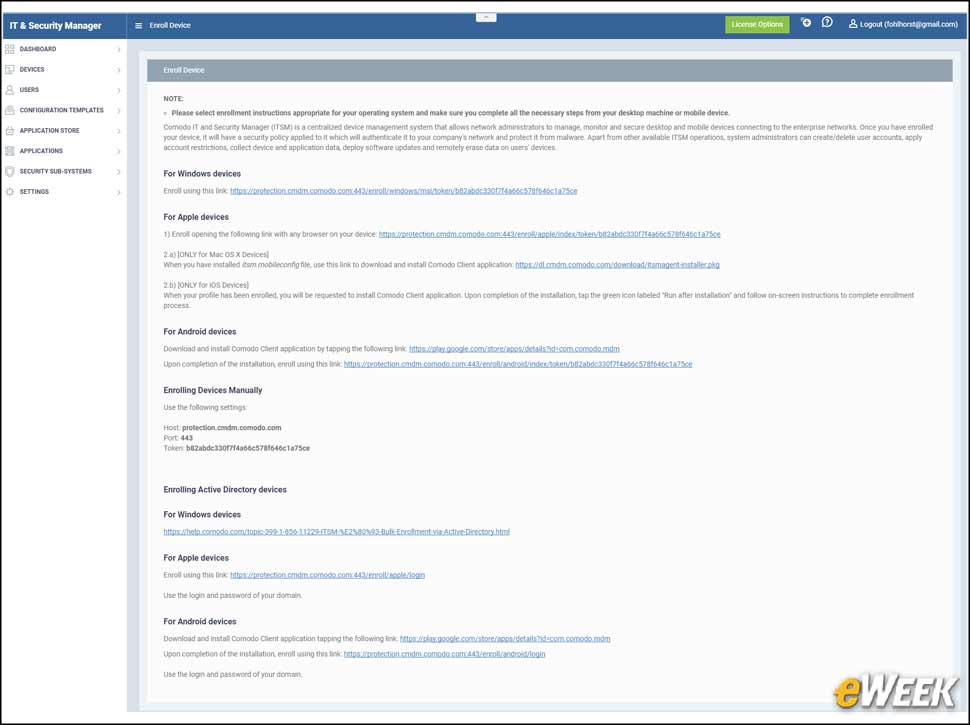
7Enrolling Devices With ITSM
End users can enroll their own devices by simply following the instructions sent via email. ITSM automatically creates a custom URL that users can visit to enroll their devices and install the Comodo Client. Administrators also have the option of creating software bundles to automate the enrollment process and automatically push the Comodo Client out to any endpoint.
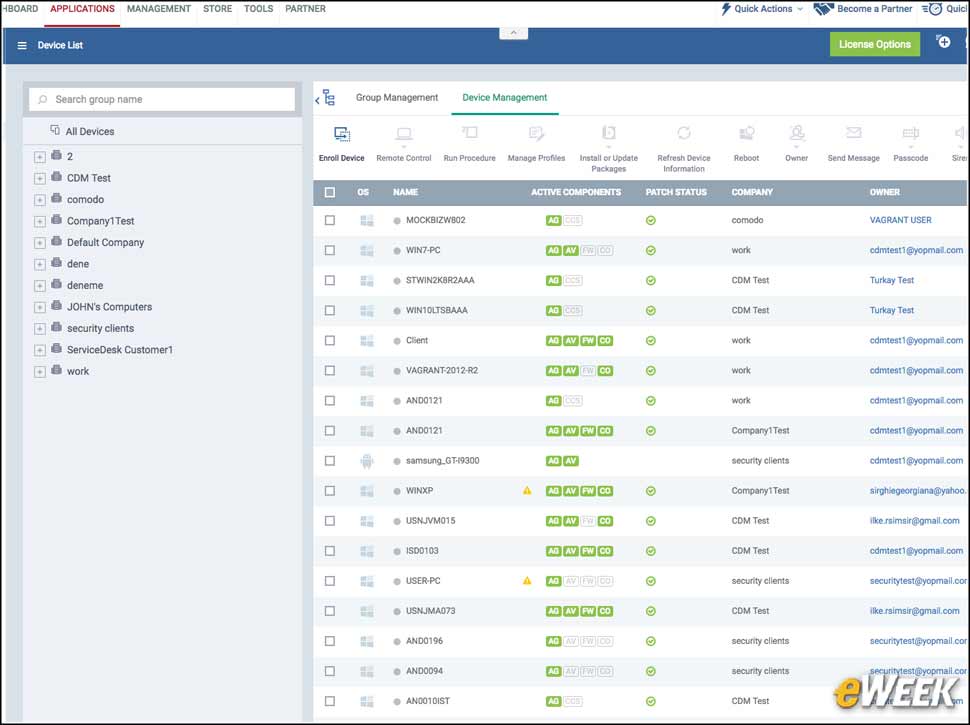
8ITSM Device List Helps With System Audits
All registered devices and their accompanying statuses are listed in the ITSM device list. From that list, administrators can drill down to get more detailed information. The list can be filtered by different criteria and customized, making it easier for administrators to spot outliers when auditing systems or going through a forensics or remediation process.
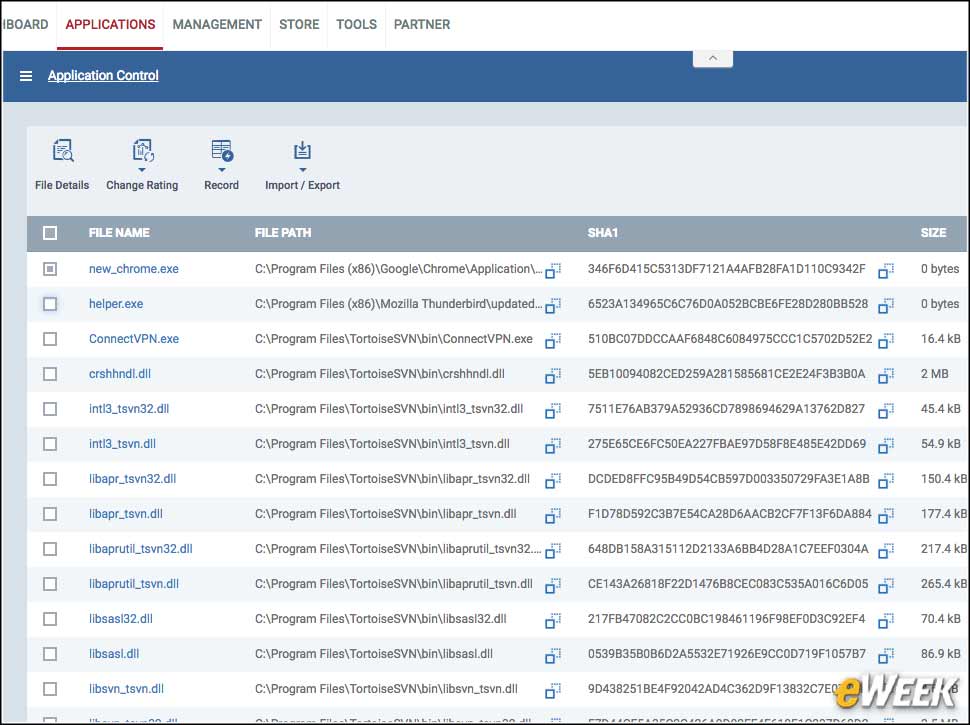
9ITSM Keeps Track of Application Status
Applications are registered with AEP as well, and administrators can browse through what applications are known by the system, the status of those applications and how those applications are rated. It can also identify unknown malware detected on the endpoints. Administrators have granular control over applications and can quickly determine where those applications are used and by what device.
10ITSM Tracks Device Antivirus Status
The security subsystems antivirus list provides a view into the antivirus status of devices attached to the network. Administrators can initiate scans and updates and take actions based upon the information presented in the list; they can also tag multiple systems. Critical information, such as malware status and scan states, is readily visible and gives administrators instant insights into the security posture of the endpoints.
11Compliance Status
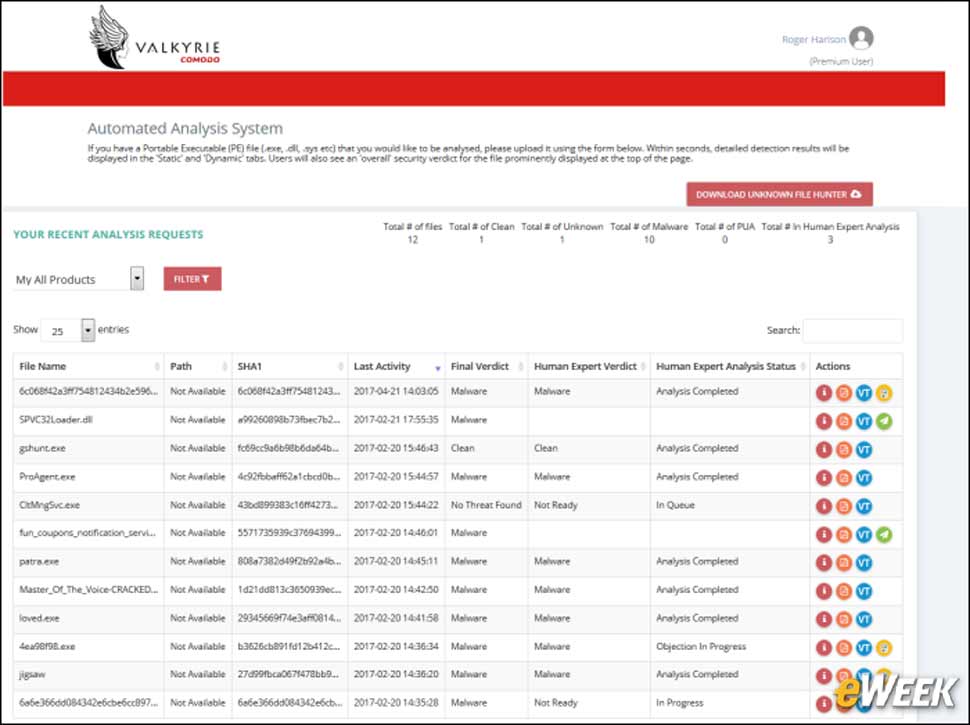
12Comodo Valkyrie Continually Analyzes Files
Valkyrie is the online portion of AEP’s file analysis capabilities and offers the ability to continually analyze files and determine if those files are a threat. Unlike a signature-based solution, Valkyrie goes many steps further by looking into a file’s payload, functions and activities. That gives zero-day protection from rapidly spreading attacks and provides extra peace of mind to administrators battling ransomware.
13Comodo Valkyrie Reporting
Valkyrie can report on multiple security concerns; one of the most valuable reports is the APT Assessment Scan, which displays the likelihood of an Advanced Persistent Threat (APT) impacting an endpoint. APTs usually prove hard to detect and eliminate. Using behavior monitoring as well as deep file scanning, Comodo AEP is able to locate APTs and inform administrators of the potential threat.