Monthly Archives: September 2018
Attivo Brings Cyber-Security Deception to Containers and Serverless
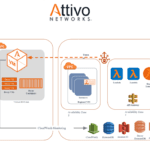
As organizations begin to embrace container and serverless technologies, there is a corresponding need to secure those deployment models. On Sept. 24, Attivo Networks...
Yubico Advances Strong Authentication Security With YubiKey Series 5
Yubico announced its 5 Series security keys on Sept. 24, providing organizations with enhanced hardware to improve authentication security.Yubico develops a hardware-based authentication device...
Virtual Analyst for Adobe Analytics Helps Uncover Customer Insights
With companies accumulating customer data at an unprecedented rate, it’s getting harder to find and analyze the key trends and insights that could impact...
IT Science Case Study: Keeping Virtual Machines Running 24/7
Here is the latest article in the eWEEK feature series called IT Science, in which we look at what actually happens at the intersection of...
Eight New Technologies That Are Changing Video Production
It’s pretty easy to take new-gen video for granted. We haven’t always had IMAX theaters, 3D movies and augmented reality applications; this has only...
Despite a Lack of Deployment, AI Viewed as Top Talent Management Tool
Despite a Lack of Deployment, AI Viewed as Top Talent Management Tool
While most organizations recognize the potential for artificial intelligence (AI) solutions as game-changing...
iOS 12 Improves Security, Performance of iPhones, iPads
Today’s topics include Apple improving mobile devices’ security and performance with iOS 12, and Lenovo partnering with NetApp to add stronger flash capabilities.Apple recently...
DigiCert, Gemalto, ISARA Partner on Quantum-Safe Encryption
While quantum computing could potentially enable new innovations and models for IT, it also represents a looming challenge for IT security, as existing forms...
Cloudflare Secures Time With Roughtime Protocol Service
If time is money, then how important is it to secure the integrity of time itself? Time across many computing devices is often synchronized...
Visualize This: How to Make the Most Effective Use of Data
If you’ve been reading my eWEEK storage coverage during the last 13 years, you’ll note that the most common thread in all those articles...